This HTML code snippet contains an image tag aligned to the right. The image, with a class of “size-medium,” is sourced from a specific URL and has specified dimensions of 300 pixels in width and 235 pixels in height.
In the provided code snippet, there is a nested structure with an image aligned to the right. The image source points to an external URL, and it is displayed at a medium size of 300×235 pixels.
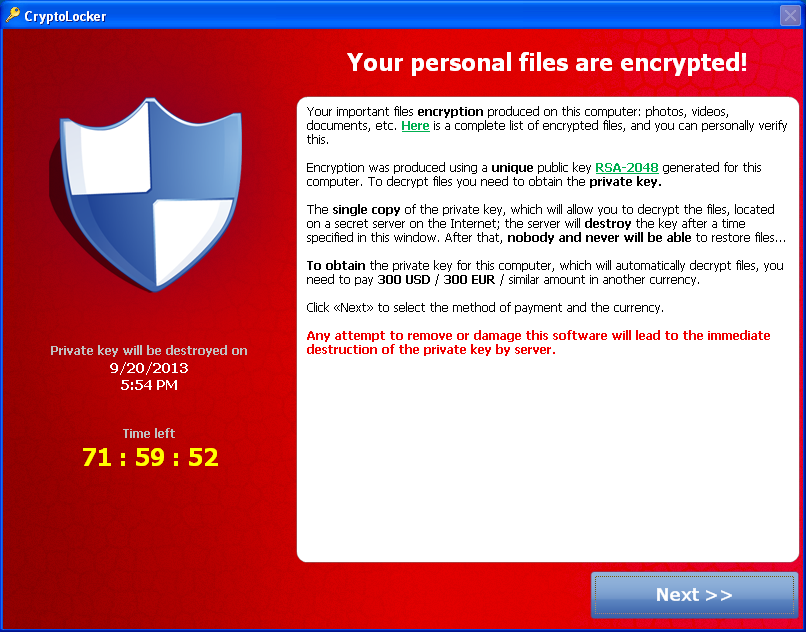
Displayed here is the image of the CryptoLocker User Interface as shown by Dell SecureWorks.
Since its introduction in early September of this year CryptoLocker has made headlines by preventing its victims from accessing their own files. According to analysis by Dell SecureWorks the number of CryptoLocker victims has grown into the hundreds of thousands, with the exact number likely to be above 250,000.
All of these infected computers add up. While not everyone pays to ransom demanded by CryptoLocker the small percentage that do have made cybercrime a very profitable endeavor for the group behind the malware. Current estimates suggest that in Bitcoin payments alone the group has grossed more than $300,000. And it’s very likely the group has earned far more than this, as Bitcoin is only one payment method offered and is more difficult to acquire than other options.

CryptoLocker infection rates show no sign of slowing. While CryptoLocker originally spread only by targeted emails to high-priority businesses, in recent weeks it has been spread largely by botnets and professional exploit kits. This means that the individuals behind CryptoLocker are likely paying other malware owners to infect new machines with CryptoLocker for them.
While CryptoLocker may change in the future, computer users should know that there are precautions that can be taken to prevent CryptoLocker infections. If nothing else, having up-to-date backups of your important files could save you hundreds this holiday season.